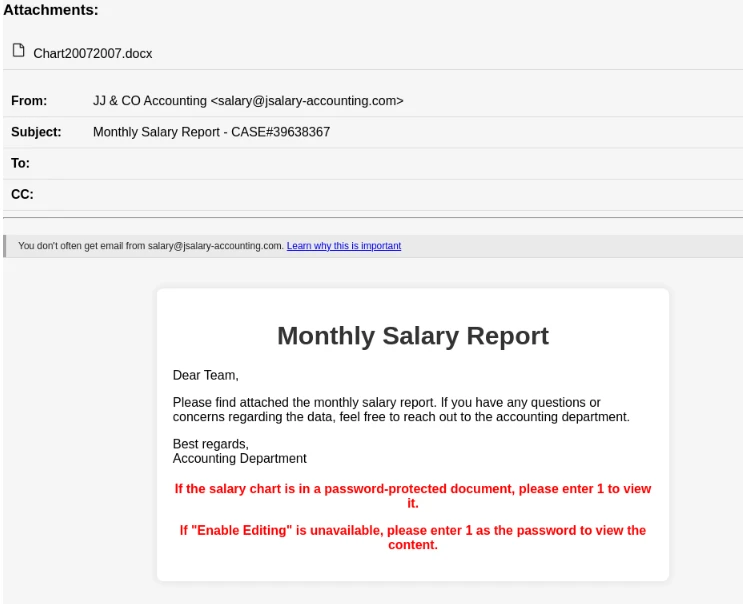
The PhantomBlu campaign employs sophisticated phishing tactics, masquerading as emails from legitimate accounting services. These emails, distributed through the SendInBlue or Brevo platform, contain attachments purportedly containing monthly salary reports in Office Word format (.docx). Recipients are instructed to download the attachment and enter a provided password to view a “salary graph” hidden behind a clickable printer image.
However, this image is a disguised Object Linking and Embedding (OLE) package, exploiting a Windows feature for data sharing between applications. Clicking the printer icon activates OLE template manipulation, revealing an archived .zip file housing a PowerShell dropper. This dropper executes a script upon interaction, installing the NetSupport Remote Access Trojan (RAT) and ensuring its persistence through a registry key.
The NetSupport RAT, derived from a legitimate remote desktop tool, NetSupport Manager, enables attackers to infiltrate systems for future exploitation. Once deployed, the RAT can surveil user activity, log keystrokes, transfer files, hijack system resources, and propagate through networked devices, all while masquerading as benign remote support software.
It’s worth noting that other threat actors have previously exploited CVE-2023-36025, a vulnerability in the Windows SmartScreen component, to deliver the NetSupport RAT. This highlights the sophistication and adaptability of cyber threats, as attackers continually evolve techniques to evade detection and compromise systems. The PhantomBlu campaign underscores the importance of robust security measures and user vigilance to mitigate the risks posed by such advanced phishing attacks.
Source: https://www.helpnetsecurity.com/2024/03/22/emails-delivering-netsupport-rat/